If you have landed on this page, you are lkely interested in setting up SNMP monitoring for System Center Operations Manager 2012 and have probably been frustrated with the lack of consolidated information or even outdated information found on the Internet. Prepare for a quick and accurate guide to get you trapping SNMP events in no time! I have labeled this Part-2, though there is no Part-1 just yet. I presume that you have taken steps to already discover devices in SNMP and now want to start seeing what type of traps are being generated from those systems. If you haven't been that far yet, let me know and I will post some resources.
First thing is first, despite what you may have read up until now, you still need to have the SNMP service running on the management server that is receiving the traps, do not disable the SNMP service. The TRAP service should be installed but turned off. This contradicts almost every other blog out there but we could not get traps coming in until we turned the service back on, period. Try the enclosed methods first and if you want to toy around, go from there, but I cannot guarantee that you'll be able to get traps if you disable both services. Additionally, to test traps, we setup a basic CentOS system running SNMP. We added the device to SCOM under networking devices. We did not install the LINUX agent.
- Open up the Windows Server Manager, then select Features and on right, select "Add Features"
- Select SNMP Service along with SNMP WMI Provider, you will have to expand to in order to select that additional component.
- Select "Install" and wait for the installation to complete.
- Open services.msc via the run prompt, or through the server manager. Scroll down until you see the SNMP services. Disable the SNMP Trap service as shown.
- Double-click the "SNMP Service" to open the property settings.
- In the SNMP Services Properties window, select the option to "Accept SNMP packets from any host" and then input a community name, such as "public".
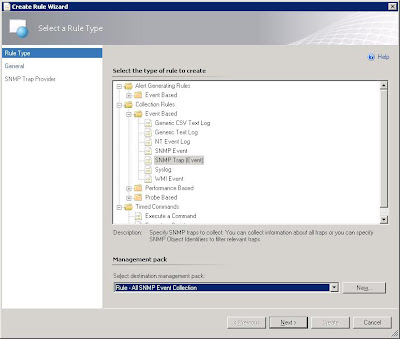
- Open the Operations Managre console, select Authoring and then rules. Right-click on Rules in order to create a new rule
- In the initial Create Rule Wizard, expand "Collection rules"->"Event based" and select the "SNMP Trap (Event)".
- Select to view all targets, then look for node type.
- Your rule should look like this now, a rule name that you have provided, the category of "event collection" and a rule target of "Node".
- For now, you have to input an OID as the screen will not take a blank OID. The one below is generic and can be used for now (1.2.3.4.0).
- Go back to the authoring screen and change the scope to Node so that you can find the newly created rule more easily.
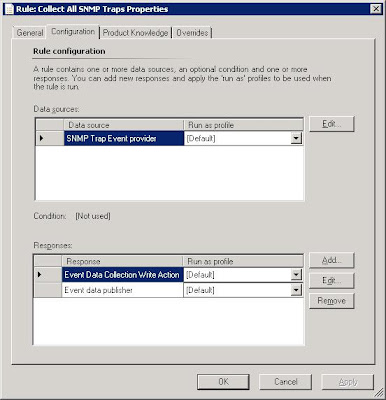
- Right-click and select properties or double-click the new rule you just created.
- Under the "Data sources" option, select "Edit".
- Now clear the previously entered OID and select OK.
- Now navigate to the "Monitoring" screen in the Operations Manager Console. Let's create a folder to group our SNMP alerts and collections to make them easy to find. Right-click the top tree labeled "Monitoring" and select "New -> Folder".
- Select the newly created folder and lets add a new event view to that folder.
- Narrow the scope to show data related to "Node" objects.
- For your "Select conditions" show information generated by rules and select the new rule that was created earlier.
- Now, generate a trap. In this case, we're using CentOS 6.2 to generate a simple version 2c SNMP trap to send to the SCOM server.
- If all is well, you should see those traps show up in the SNMP event window.
If you do not see SNMP events showing up, then it is likely your local SNMP service is not functioning correctly or needs to be reinstalled. I will add a couple of great troubleshooting blogs in a few days.



















This worked for me. Thanks a lot.
ReplyDeleteGlad it helped!
DeleteIn this example, for SCOM to accept the trap does the device generating the trap need to be discovered and configured within SCOM or will SCOM accept a trap from any device sending traps to it?
ReplyDeleteThe device will have to be discovered first in SCOM to receive and recognize the trap source. You can find how to setup a device over on this link: http://kevingreeneitblog.blogspot.com/2012/01/scom-2012-network-monitoring-magic.html
DeleteIm still not getting any snmp traps in, would love to see some more troubbleshooting on this.
ReplyDeleteWorking on a soup to nuts way to test out SCOM. Retracing me steps and getting screen shots. Hope to have a follow-up in a couple of days :)
DeleteThank you for the good guide!
ReplyDeleteHowever, it's not working as expected at the moment.
Can see that the process "MonitoringHost.exe" is listening on UDP:162. Running a packet sniffer on the SCOM server shows that the traps are getting to the machine.
The only difference is that my network device has been setup with an access method of ICMP only, as it doesn't respond to SNMP on port 161.
Does the device have to be a network device ? or can you monitor a Windows server ?
thank you!
John, the device has to be a LINUX or network device in order to monitor SNMP (basically, non-windows). If you try to monitor a Windows server, SCOM will pick that up and ignore the requests. If you want to receive traps from windows servers, you can setup a LINUX SNMP relay and monitor the LINUX server as a network device. I will have an upcoming article on how to do that. Is the device you are having problems with Windows based?
ReplyDeleteHi Dave, Thanks for the reply.
DeleteThe machine in question is indeed a Windows server. Although it is defined as an ICMPOnly Network device. Will SCOM still pick up that it is Windows machine, even when defined as a network device ?
I suppose that is an option and I'd be very interested in that article, but it doesn't make sense (to me) that MS wouldn't allow SCOM to monitor traps from a Windows machine.
thanks :)
Correct, even with ICMP only, as soon as SCOM realizes it is a windows server, it ignores any monitoring requests. I went round and round on this as well, even escalating to the SCOM support group and that was their response. We originally wanted to capture SNMP alerts coming from our Windows based VMWare vCenter server. Seems a bit shortsided to me. I ended up routing those alerts through LINUX instead. How is that for irony? If I want to process my Windows SNMP events, I have to route through LINUX. You should be able to see in the discovery log messages that pick up the windows server and then quite literally say the system is being ignored. I will see if I can reproduce the issue and try to get that posted with some screen shots on my upcoming troubleshooting article.
DeleteMight seem a silly question, but where are the discovery logs ? Just started working with SCOM and it doesn't seem to do much logging.
DeleteIf you open the Operations Manager monitoring console, then expand the "Operations Manager" folder and then expand "Network Discovery", you'll see an event monitor folder called "Network Discovery Progress Events"
DeleteFor normal devices, an event will get logged with the following verbiage "No devices were found in filtered list after discovery". If a filtered device was found, such as a windows server, it would say filtered devices were discovered and they would be excluded from SNMP monitoring.
Under event number 12008 in that same view, you'll see the discovered device. In there, you'll see something that says "Windows computers filtered" for any windows devices that were discovered via the SNMP discovery process.
Hi Dave,
DeleteI have discovered my linux machine as a network device, sending traps from a win machine to this linux machine which relays it back to the win machine where scom is installed. I can see the packets coming from the Linux source to the windows target but I do not see any events in SCOM. What should I do...
Not sure if UNIX is going to differ much from LINUX. Check this link out that might help: http://serverfault.com/questions/81077/how-to-configure-snmp-for-snmp-trap-forwarding
ReplyDeleteThanks Dave, finally got this working.
DeleteNext to wrestle with the vendor of our SNMP temp monitor who can't understand that their device sends invalid traps ...
Hi John did you fix the issue ? i have the same issue i need to process windwos SNMP event .please help me.
ReplyDeleteErickson, where are you stuck in the process?
ReplyDeletehello i have do all you write here but I have problem with scom I see that snmp traps ar come to server with wireshark and it retursn but in scom I couldnot see events .can you give me some simple mp or configuration of scom?
ReplyDeleteI have a blog post pending on just this type of troubleshooting. Hoping to finally get it out soon. It will be a two part series, but give you a way to validate the setup end-to-end. Look for that soon.
ReplyDeletehave you write some post ?
ReplyDeleteHi Dave, me again.
ReplyDeleteJust going back to this, did you find that you needed to set the server up as a ICMP and SNMP device within the network discovery?
Reason I ask is that I've got the requirement to monitor a Suse server which sends out traps, but is not configured for SNMP (i.e. doesn't respond to probes). I've set this up correctly and can see traps in wireshark, but no alerts are create in SCOM.
Any ideas?
What version of Suse? and is there any way to configure SNMP or is that a non-starter? Otherwise, I've been setting servers up as SNMP only. I've had mixed results when using ICMP or SNMP when attempting to capture SNMP traps from systems I want to monitor. One of the things I'm finding is that it seems much easier to use a program like Solarwinds, which can import MIB files, to capture the SNMP traffic and then send the alerts to SCOM. As I continue to work with SNMP in SCOM, it has many limitations that I find frustrating. Works great for Cisco devices but falls short beyond that.
ReplyDeleteIt's Suse Enterprise Server 11, so configuring SNMP will work fine, just would rather not fettle with a production server. I can see that other network devices (switches and the like) raise traps via this rule perfectly, so it must be as this server is defined as ICMP only.
DeleteAgreed, SNMP in SCOM is very frustrating. Unfortunately I don't have the luxury of using something else like Solarwinds. I've just moved away from SNMP as much as possible (SCOM now monitors the event logs which the application is configured to write to, for example). Using event monitors and Windows stuff allows you to use repeated event monitoring, which is actually really good.
Hi Dave, can you please explain how SolarWinds can be configured to send the alerts (SNMP traps) to SCOM?
DeleteHi, I am still having problems with this. I have setup a rule as above, and also a view. I am using SCOM 2012, and been told to disable windows SNMP service as SCOM 2012 has built in trap monitor. I am not receiving an alert, and had a ticket open with Microsoft for a week now, and we are still unable to resolve. Has anyone got any tips?
ReplyDeleteIf you look at my first paragraph, that is the behavior I also experienced when not setting up the local SNMP service. If you want to be able to use the event log to check for activity, you'll have to setup local SNMP services. Otherwise, you'll need to set the SNMP monitor to simply generate an alert for all the traps. That would allow you to see what's working and what's not.
DeleteI'm also available for hourly consulting if you'd like some assistance getting it squared away.
DeleteThis comment has been removed by the author.
ReplyDeleteHi there,
ReplyDeleteExcuse my ignorance but is there a way for the SCOM to perform SNMP GETs instead of the pooling (SNMP Traps)?
Absolutely, you can perform SNMP probes with unit monitors and rules
DeleteCould you go into a little more detail or point to someplace where this is documented?
DeleteSeems that this is no longer a viable option if you use Server 2012 or server 2012 R2 as SNMP is deprecated as a role.
ReplyDeletehttp://technet.microsoft.com/en-us/library/hh831568.aspx
Adding SNMP as illustrated in the first portion may not be viable. I show that it works even without native SNMP. The difficulty is that the event view that I setup doesn't work in the same manner, making it somewhat more of a pain to troubleshoot. Instead, you can setup critical or warning alerts and they will show up in the default console. With SNMP, it's a bit more elegant in that you can watch all the events in the event pane without generating the alerts. I haven't been able to get that same functionality without SNMP.
DeleteHi Dave,
ReplyDeleteas I inherit our SCOM 2012 installation from another admin 6 month ago I've learned a lot about this product. Because I'm a Linux and Unix guy with a little HP OpenView TeMIP and Micromuse Netcool background I find it very interesting how SCOM works and differs from all other monitoring systems. To make this popular I've published a bunch of documents which I want to share. Most of them are about Linux integration and one of them will tell the story how it is possible to integrate VMware vSphere server running on windows sending snmp traps to SCOM. I hope you will find these information valuable. You can find it here:
http://www.fricnet.de/
This comment has been removed by a blog administrator.
ReplyDeleteHello Dave, I'm glad i stumbled on this succinct article of yours around monitoring network devices using SNMP trap...Great job man. However, i need your insight and thought path around how xSNMP for ATM monitoring that was available in SCOM2007 can be used or modified to be adapted to SCOM2012. I'll be glad to hear from you soonest. Thanks.
ReplyDeleteCan you please explain which event log shows the incoming traps when configuring the SNMP service as described here?
ReplyDelete